Axipro Highlights
- All Blog, Axipro Vault
- Feb 27, 2025
- All Blog, Axipro Vault
- Feb 20, 2025
- All Blog, Axipro Vault
- April 21, 2025
Search our Resources
Our Resources

- All Blog, Drata, DRATA-blog
The compliance landscape in 2026 is more intricate than ever,..

- All Blog, SOC 2
SOC 2 compliance can sometimes feel like a needlessly complex..
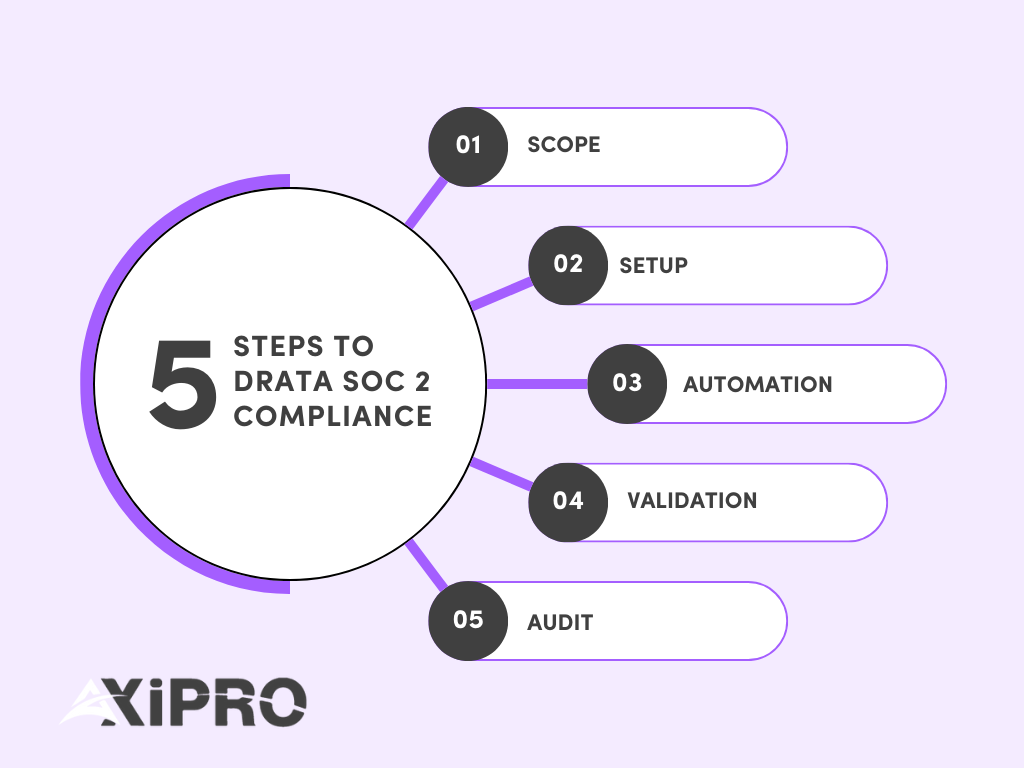
- All Blog, Drata, SOC 2
Drata is a powerful tool. It can transform a slow,..

- All Blog, SOC 2
If your company sells software, handles customer data, or operates..
- All Blog, SOC 2
Share This Post Table of Contents read iso case studies..

- All Blog
Share This Post Table of Contents read iso case studies..

- All Blog
Share This Post Table of Contents read iso case studies..

- All Blog
Share This Post Table of Contents read iso case studies..

- All Blog
Share This Post Table of Contents read iso case studies..

- All Blog
Share This Post Table of Contents read iso case studies..

- All Blog
Share This Post Table of Contents read iso case studies..

- All Blog, Pentest
What Is Penetration Testing? A Practical Guide to Methods, Timelines,..