Share This Post
Watch Video
Don’t wait until a breach happens. Watch our Loom video tutorial to get started today!
What is a Tabletop Exercise?
A cybersecurity tabletop exercise is a structured, discussion-based session where an organization’s key stakeholders collaborate to assess and improve their response to cybersecurity incidents. Led by a facilitator, these exercises simulate real-world security events in an informal setting—either in a conference room or virtually. The primary goal is to test an organization’s readiness, refine incident response (IR) and disaster recovery (DR) strategies, and ensure that all team members understand their roles and responsibilities during a cyber crisis.
At Axipro, we believe that preparation is the key to resilience. These exercises aren’t just about compliance; they help teams build confidence, refine their strategies, and ensure that in the face of an attack, everyone knows exactly what to do.
Why Are Tabletop Exercises Important?
Tabletop exercises play a crucial role in strengthening an organization’s cybersecurity posture by:
- Testing Incident Response & BCDR Plans: Identifies gaps in IR and Business Continuity & Disaster Recovery (BCDR) plans, allowing organizations to proactively address weaknesses before a real attack occurs.
- Reducing Recovery Time & Costs: A well-prepared response can significantly minimize downtime and financial losses, potentially saving thousands in cybersecurity recovery fees.
- Meeting Compliance Requirements: Regulatory frameworks such as ISO 27001, SOC 2, and CyberSecure Canada mandate conducting tabletop exercises as part of security protocols.
- Enhancing Coordination & Decision-Making: Participants gain clarity on their roles, enabling the organization to react effectively and efficiently to an incident.
How to Conduct a Tabletop Exercise
Step 1: Define Your Objectives
Before initiating a tabletop exercise, establish clear objectives such as:
- Assessing the organization’s ability to respond to a ransomware attack.
- Evaluating data recovery and communication protocols.
- Testing coordination between IT, management, and compliance teams.
Step 2: Develop a Realistic Scenario
Tailor the scenario to threats relevant to your organization. Examples include:
- A ransomware attack crippling critical systems.
- Unauthorized access to customer data.
- Cloud service disruptions impacting business continuity.
Step 3: Assign Roles
Assign specific roles to participants, such as:
- Incident Response Team Lead – Coordinates the overall response.
- IT Security Specialist – Investigates and mitigates threats.
- Communications Coordinator – Manages internal and external messaging.
- Executive Decision Maker – Makes key business-impacting decisions.
Step 4: Facilitate the Exercise
The facilitator should guide the discussion and encourage active participation. Key takeaways to document include:
- The speed of incident detection and response.
- Gaps in policies, communication, or technical capabilities.
- Recommended improvements to strengthen future incident response.
Step 5: Review & Improve
After the exercise, analyze findings and implement necessary changes to IR and DR plans to enhance preparedness.
Sample Tabletop Exercise Scenario
Scenario: Cyberattack on a Cloud Platform
Scenario Overview
Axipro, a trusted cybersecurity solutions provider, is helping a mid-sized cloud solutions company navigate a major cybersecurity breach, impacting thousands of customers.
Incident Description
- 10:15 AM: The IT team detects suspicious activity via an intrusion detection system.
- 10:30 AM: Executives report inaccessibility to email and critical applications.
Security Breach & Platform Outage
- The attack leads to a complete outage of the company’s primary platform.
- Investigation reveals threat actors deployed malware on critical systems.
- Sensitive customer data, including financial records and proprietary software code, is compromised.
Response Actions
- The incident response team isolates compromised systems.
- The disaster recovery plan is activated to restore platform functionality.
- New instances of production environments are deployed to replace affected infrastructure.
Key Considerations for Response & Recovery
Incident Response (IR) Exercise
At Axipro, we understand that incident response isn’t just about reacting to attacks—it’s about preventing them before they happen. Our IR exercises test an organization’s procedures and technical capabilities for identifying and responding to cyberthreats, security breaches, and cyberattacks. A strong IR strategy helps cybersecurity teams detect and contain threats, recover systems quickly, and reduce financial and reputational damage.
Disaster Recovery (DR) Testing
A DR test helps identify risks affecting business operations and prioritizes recovery efforts based on the severity of outages. Understanding how an outage impacts the company and its customers is critical to making informed decisions about asset protection and risk management.
Business Impact Analysis

Key Systems and Processes
The following table outlines critical systems and their downtime estimates in a disaster scenario.
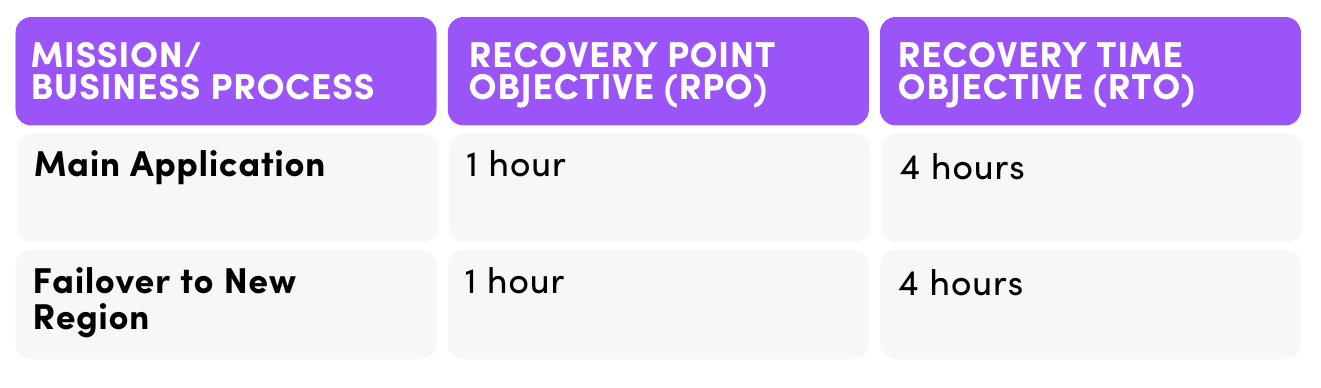
Estimated Downtime Considerations
- RTO (Recovery Time Objective): The maximum acceptable downtime before operations resume. It includes time for disaster declaration, system setup, recovery execution, backup access, data transfer, and system restart.
- RPO (Recovery Point Objective): The acceptable amount of data loss measured in time. It defines the latest recovery point, ensuring data can be restored from backups without unacceptable loss.
Rules for the Exercise
- Everyone is encouraged to contribute.
- Silence indicates agreement.
- The scenario may evolve as needed.
- This is a learning exercise, not a test.
- The facilitator can table issues for later discussion.
- No outside interruptions are allowed.
- All opinions and discussion points are respected and welcomed.
Final Thoughts
At Axipro, we believe in proactive security. A well-executed tabletop exercise isn’t just a compliance requirement—it’s a lifeline in today’s evolving cyber threat landscape. By rigorously testing your IR and DR plans, your organization can mitigate risks and improve its overall cyber resilience.