SOC 2 compliance can sometimes feel like a needlessly complex Pandora’s box of documentation. But it shouldn’t be. That’s why today, we’ll show you how to easily become compliant with our 12-step SOC 2 compliance checklist.
In its simplest form, all the SOC 2 sections point to the same question:
Can you prove your controls work?
This SOC 2 Compliance Checklist guides you through the process from scoping through audit completion for both SOC 2 Type 1 and Type 2. It is practical, auditor-aligned, and written for teams that want clarity rather than theory.
If you want the short version: SOC 2 is not about tools or paperwork. It is about repeatable processes, clear ownership, and evidence that stands up to scrutiny.
What is a SOC 2 compliance checklist?
A SOC 2 compliance checklist is a structured roadmap that maps your internal controls to the AICPA Trust Services Criteria and prepares your organization for a Type 1 or Type 2 audit.
For a full breakdown of SOC 2 requirements, read our detailed SOC 2 guide.
How to Use This SOC 2 Compliance Checklist
Think of this checklist as a living roadmap, not a one-time document. You should revisit it at four points: before scoping, during readiness, throughout evidence collection, and after the audit for continuous compliance.
Type 1 vs. Type 2: Which Checklist Items Change?
The core checklist does not change dramatically between Type 1 and Type 2. What changes is time and proof.
Type 1 evaluates whether controls are designed correctly at a specific point in time. Type 2 evaluates whether those same controls operated effectively over an observation period, usually 3, 6, or 12 months.
This means evidence for Type 2 must show consistency, such as quarterly access reviews, repeated vulnerability scans, and incident response tests that actually occurred.
Who Owns Each Workstream
SOC 2 is cross-functional by design. Security may lead, but it cannot succeed alone.
Engineering typically owns secure SDLC, change management, and logging. IT owns IAM, endpoints, and device management. Legal and HR contribute policies, onboarding controls, and training. GRC or compliance coordinates risk assessment, evidence, and auditor communication.
The fastest SOC 2 projects have named control owners with deadlines, not shared responsibility.
What “Audit-Ready” Really Means
Being audit-ready does not mean “we think we are secure.” It means you can produce clear, dated, and traceable evidence that maps directly to the Trust Services Criteria.
Auditors test design, then operation. They expect policies, tickets, screenshots, logs, and approvals. They also expect alignment. If your policy says quarterly, your evidence cannot show annual.
The AICPA provides the underlying standard, supported by SSAE 18 and AT-C 205.
Pre-Checklist: Confirm You Actually Need SOC 2
Not every company needs SOC 2 immediately. If your customers are SMBs, you may see lighter requirements. If you sell to enterprises, SOC 2 often becomes non-negotiable.
Security questionnaires are the strongest signal. When prospects ask about penetration testing, access reviews, and incident response evidence, SOC 2 is usually the cleanest way to respond at scale.
Alternatives like ISO 27001, PCI DSS, or HIPAA can be valid. But SOC 2 is uniquely customer-facing, especially in North America. ISO 27001 is excellent for global alignment, while SOC 2 maps directly to buyer trust.
The 12-Step Checklist

Step 1- Define Scope
Scoping mistakes cause more SOC 2 delays than any missing control.
Your scope must clearly define the services you provide, the systems that support them, and the access controls. Over-scoping increases cost and complexity. Under-scoping leads to auditor pushback.
In-scope systems usually include production cloud environments, CI/CD pipelines, support tooling, and identity providers. In-scope people include employees and contractors with access to customer data. Third parties are addressed as Subservice organization, using either the Carve-out method or Inclusive method.
Data classification and flows must identify PII, PHI, or payment data, and how it moves through systems.
Action Plan for Scoping
- Define the Service Commitment
- List In-Scope Systems
- Identify In-Scope People
- Document Third Parties
- Map Data Flows
- Validate Scope with Leadership
Step 2- Select the Trust Services Criteria
All SOC 2 reports include Security (Common Criteria). The others are optional but must be justified.
Availability focuses on uptime and disaster recovery. Confidentiality focuses on sensitive data protection. Processing Integrity focuses on system accuracy. Privacy applies when personal data obligations are central.
Your report must document why each criterion is included or excluded. Auditors look closely at this rationale.
Trust Service Criteria Action Plan
- Confirm Security (Mandatory)
- Assess Optional Criteria
- Document Inclusion Rationale
- Obtain Executive Sign-Off
Step 3- Choose the Audit Path and Timeline
Most teams benefit from a readiness assessment before audit. This is often referred to as a Readiness assessment or Gap analysis.
Type 1 audits can be completed in weeks once controls are ready. Type 2 timelines depend on the observation period. Six months is the most common balance between speed and credibility.
Define control owners early and create an evidence calendar. Late evidence is the enemy of clean audits.
Audit Path and Timeline Action Plan
- Conduct Readiness or Gap Assessment
- Choose Audit Type
- Set Observation Period (Type 2)
- Assign Control Owners
- Build Evidence Calendar
Step 4- Pick an Auditor and Define the Engagement
Choose a CPA firm with real SOC 2 experience in your industry. Responsiveness matters more than brand name.
Confirm standards, testing approach, sampling expectations, and how subservice organizations are treated. The engagement letter should clearly state scope, period, and deliverables. A clear PBC list process avoids confusion later.
Action plan for finding an auditor.
- Shortlist CPA Firms
- Review Testing Approach
- Clarify Subservice Treatment
- Finalize Engagement Letter
- Request Preliminary PBC List
Step 5- Perform a SOC 2 Gap Analysis
Map existing controls to the Trust Services Criteria. Missing policies, undocumented processes, and inconsistent evidence usually surface here.
Prioritize high-risk gaps first. Document known exceptions and compensating controls honestly. Auditors prefer transparency over perfection.
Gap Analysis Action Plan:
- Map Controls to Criteria
- Identify Missing Controls
- Prioritize by Risk
- Document Compensating Controls
Step 6- Build the Policy and Governance Foundation
Policies should reflect reality. Information security, access control, change management, incident response, vendor risk management, and BCDR must all exist, be approved, and be followed.
If Privacy is in scope, privacy notices, data handling, and retention policies must align with actual practices.
Governance Action Plan
- Draft Core Policies
- Align Policy to Reality
- Obtain Formal Approval
- Train Staff
Step 7- Implement Security (Common Criteria) Controls
This is where most effort goes. IAM, MFA, SSO, and RBAC must be enforced, not optional. Logging, monitoring, vulnerability scanning, and patch management must be operational.
Auditors expect encryption in transit and at rest, typically supported by KMS. Secure SDLC, change management, incident response, risk assessment, vendor reviews, and physical security all fall under this umbrella.
Common Control Implementation Action Plan
- Enforce Identity Controls
- Enable Monitoring
- Implement Vulnerability Management
- Encrypt Data
- Operationalize Secure SDLC
- Run Risk Assessment
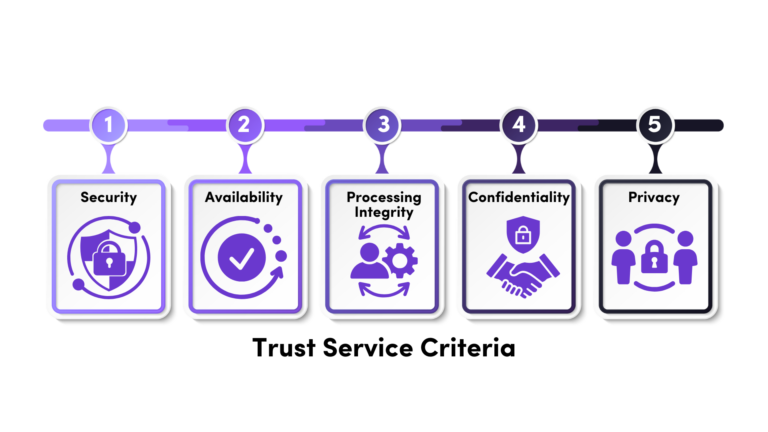
Step 8- Availability, Confidentiality, Processing Integrity, Privacy
Only implement what is in scope. Availability requires uptime definitions, monitoring, and tested disaster recovery. Confidentiality focuses on data handling and disposal. Processing Integrity requires evidence that systems do what you promise customers. Privacy requires DSAR handling, consent, and cross-border controls.
Availability
- Define uptime commitments.
- Document monitoring thresholds.
- Test BCDR annually.
- Record test results and improvements.
Confidentiality
- Classify confidential data.
- Restrict access via RBAC.
- Define disposal procedures.
- Validate encryption controls.
Processing Integrity
- Document system processing controls.
- Define input validation mechanisms.
- Monitor output accuracy.
- Track customer issue resolution.
Privacy
- Publish privacy notice aligned with practice.
- Implement DSAR handling process.
- Define data retention schedule.
- Control cross-border transfers.
Step 9- Build the Evidence Package
Auditors test evidence, not intent. They expect a clear System description, control narratives, access reviews, change tickets, incident records, vulnerability scans, vendor SOC reports, training logs, and BCDR test results.
Evidence must be complete, dated, and traceable.
Evidence Package Action Plan
- Draft System Description
- Collect Control Evidence
- Ensure Traceability
Step 10 — Run Internal Reviews
Before the auditor looks, you should. Control owners should sign off. Exceptions should be documented with root cause and corrective action. Management review is not optional.
Internal Review Action Plan
- Control Owner Sign-Off
- Document Exceptions
- Management Review
Step 11 — Complete the Audit
Expect walkthroughs, sampling, and follow-up questions. Review the draft report carefully, especially scope language and subservice organization descriptions.
Audit Action Plan
- Prepare for Walkthroughs
- Respond to Sampling Requests Quickly
- Review Draft Report Carefully
Step 12 — Maintain Continuous SOC 2 Compliance
SOC 2 is not annual busywork. Continuous monitoring, periodic access reviews, quarterly vulnerability scans, annual risk assessments, and vendor re-reviews keep you audit-ready.
Teams that treat SOC 2 as a one-time project struggle with every renewal.
Maintaining Compliance Action Plan
- Schedule Recurring Reviews
- Monitor Vendor Changes
- Automate Evidence Collection
- Track Metrics
- Embed Compliance into Operations
Ready to Use This Checklist in Practice?
If you want to turn this SOC 2 compliance checklist into a clear plan with owners, timelines, and auditor-ready evidence, Axipro can help.
Our Achievement Plan guides teams from scope to SOC 2 readiness in as little as six weeks, combining human expertise with the right automation tools. Whether you need a readiness assessment, a full Type 1 or Type 2 audit, or help maintaining compliance, we simplify the process so your team can focus on growth.
Book a SOC 2 readiness call or request a checklist walkthrough today, and move from “working on compliance” to confidently audit-ready.