
About Service Organization Controls (SOC 2 Compliance)
SOC 2 Compliance is vital for service organizations handling sensitive data. It ensures they follow strict rules for security, availability, processing integrity, confidentiality, and privacy. Certified Public Accountants (CPAs) conduct thorough audits based on AICPA guidelines, resulting in Type 1 or Type 2 Certification. Type 1 Certification checks control design and implementation at one time, while Type 2 Certification examines control effectiveness over a period, often six months or more.
SOC 2 assesment reports, derived from these audits, reassure stakeholders, especially those using outsourced software storing customer data online. These reports show the organization’s commitment to protecting data integrity and confidentiality. SOC 2 Compliance confirms reliability and trustworthiness, highlighting the organization’s dedication to strong controls and security.
Service Organization Controls (SOC 2) Principles
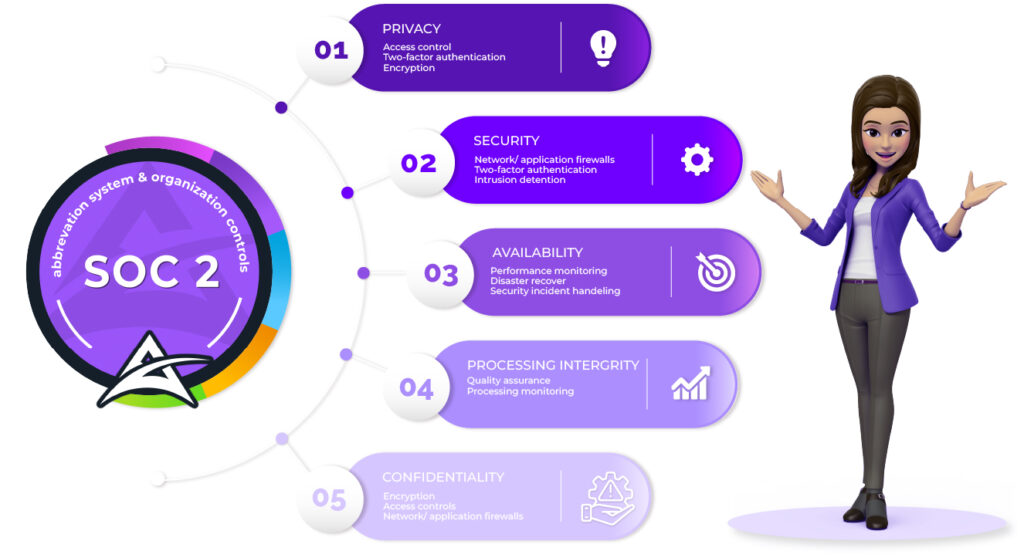

Focus of Service Organization Controls
SOC 2 compliance solution (Service Organization Control 2) emphasizes control effectiveness in security, availability, processing integrity, confidentiality, and privacy within service organizations. SOC 2 Type 1 Consultancy and SOC 2 Type 2 Consultancy aid in achieving SOC 2 Readiness. These assessments offer assurance to clients and stakeholders about the reliability, security, and privacy of services offered by these organizations.
Benefits of Service Organization Controls

Risk Assessment
Start with a thorough risk assessment to identify potential vulnerabilities and threats to your systems.
Implement Controls
Implement necessary controls and policies to address the identified risks. This may include access controls, encryption, and regular monitoring.
Documentation
Document your processes, policies, and controls. This documentation will be crucial during the audit process.
Pre Assessment
Consider a pre-assessment to evaluate your readiness for the official audit. This step helps you identify and address any gaps.
Official Audit
Engage a qualified third-party auditor to conduct the SOC 2 audit. They’ll assess your controls, policies, and overall compliance with the trust service criteria

Frequently Asked Questions
SOC 2 compliance (Service Organization Control 2) is a framework developed by the American Institute of Certified Public Accountants (AICPA) to assess and report on the security, availability, processing integrity, confidentiality, and privacy controls implemented by service organizations. It provides assurance to clients and stakeholders regarding the effectiveness of controls in place to protect their data and ensure the reliability of services.
Any service organization that processes or stores sensitive customer data on behalf of its clients may benefit from SOC 2 compliance. This includes cloud service providers, data centers, software as a service (SaaS) providers, managed service providers, and other entities entrusted with handling client information.
The Trust Service Criteria (TSCs) for SOC 2 compliance include security, availability, processing integrity, confidentiality, and privacy. These criteria serve as the foundation for evaluating the effectiveness of controls implemented by service organizations to safeguard client data and ensure the reliability of services.
SOC 2 compliance is assessed through independent audits conducted by certified public accountants (CPAs) or audit firms. During the audit process, the auditor evaluates the design and operating effectiveness of controls based on the Trust Service Criteria (TSCs). Upon successful completion of the audit, the service organization receives a SOC 2 report detailing the results of the assessment.
A SOC 2 report typically includes an auditor’s opinion on the suitability of the design and operating effectiveness of controls, along with detailed descriptions of the organization’s control environment, control objectives, and testing procedures. There are two types of SOC 2 reports: Type I reports assess the design of controls at a specific point in time, while Type II reports evaluate the operating effectiveness of controls over a specified period.


