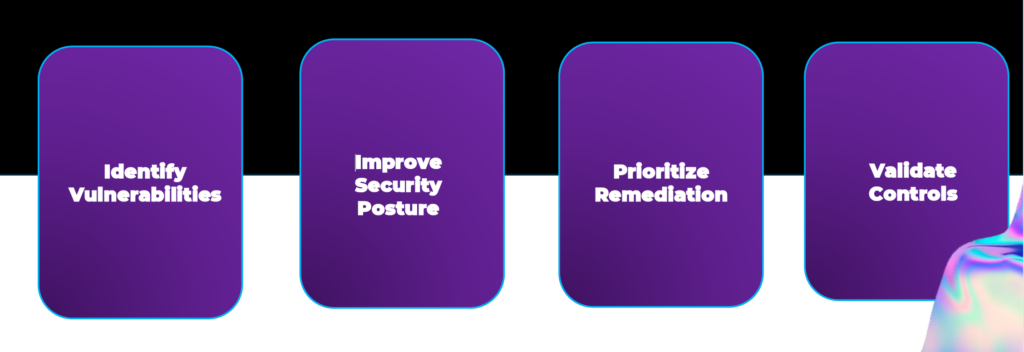
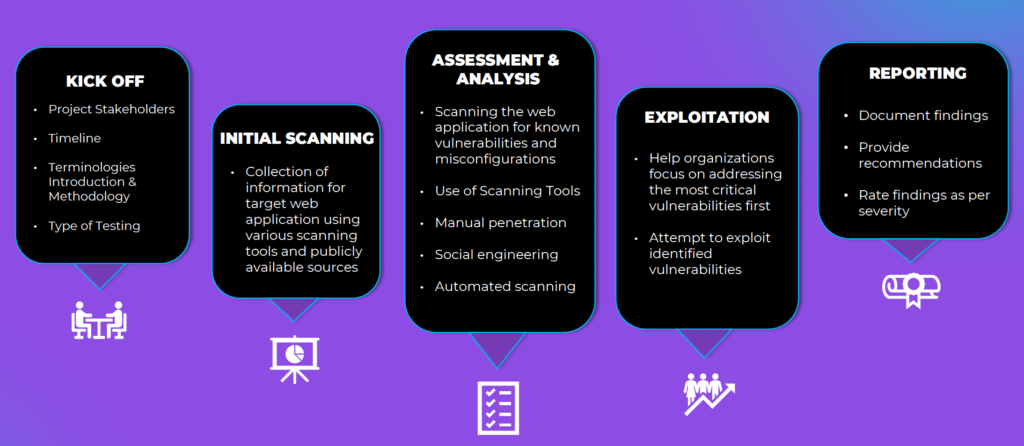
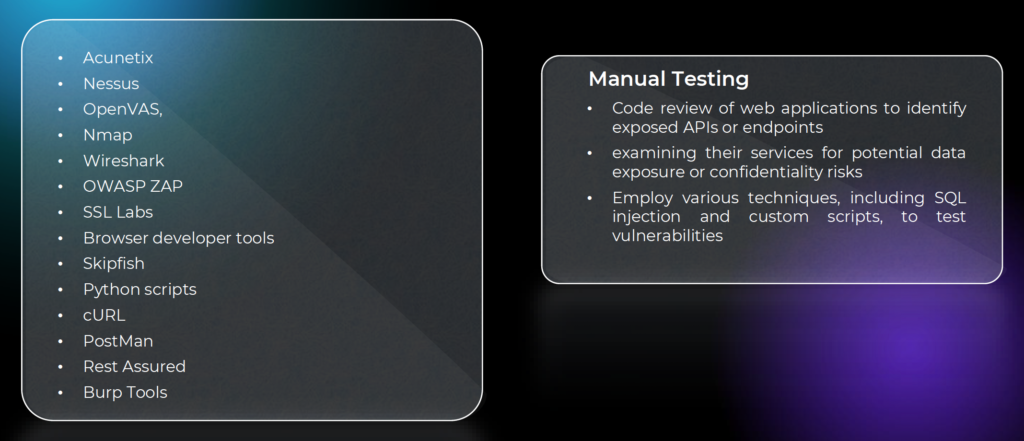
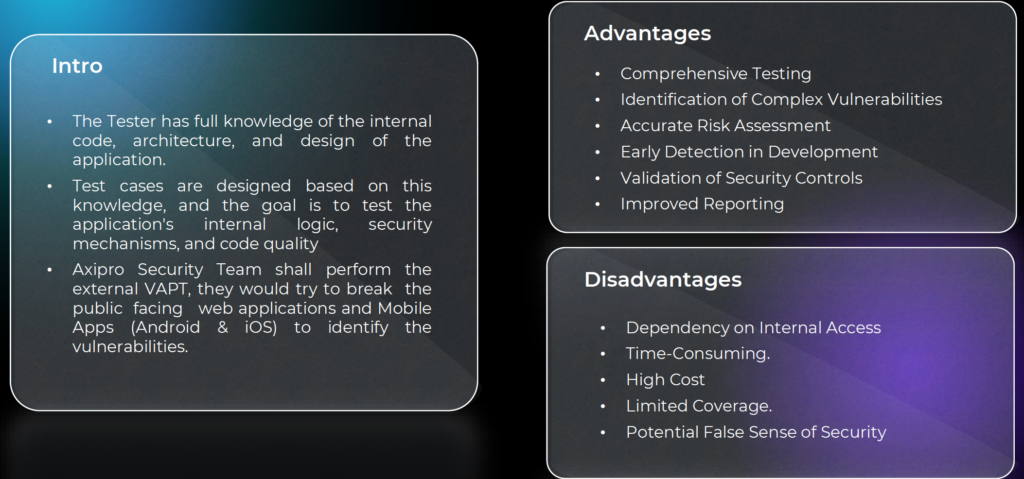
If you are preparing for certification, responding to customer security questionnaires, or simply want confidence in your security posture, penetration testing is the logical next step.
Axipro combines human expertise, structured methodology, and compliance alignment to deliver penetration testing that actually drives outcomes.
Book a consultation, request a security assessment, or speak with Axipro about integrating penetration testing into your compliance roadmap today.
At Axipro Technology, excellence is standard.