
Share This Post
Protecting your website and making it secure is essential nowadays. Among the other attacks and threats for the website, the most dangerous is the Cross-Site Scripting attacks. These attacks allow malicious actors to inject harmful scripts into trusted websites, which are then executed by the browsers of unsuspecting users. This can lead to serious consequences like stealing sensitive information, hijacking sessions, or defacing websites. In this blog, we’ll explore what XSS attacks are, the different types of XSS, their impact, and how to prevent them. We’ll also touch on the relationship between XSS and Cross-Site Request Forgery (CSRF) attacks, which can complicate web security.
Outline
A Brief Conception of Cross-Site Scripting (XSS)?
Types of Attacks
Impact of XSS Attacks
Cross-Site Request Forgery (CSRF) and Its Relationship with XSS
Prevention Strategies Against XSS
Conclusion
A Brief Conception of Cross-Site Scripting (XSS)?
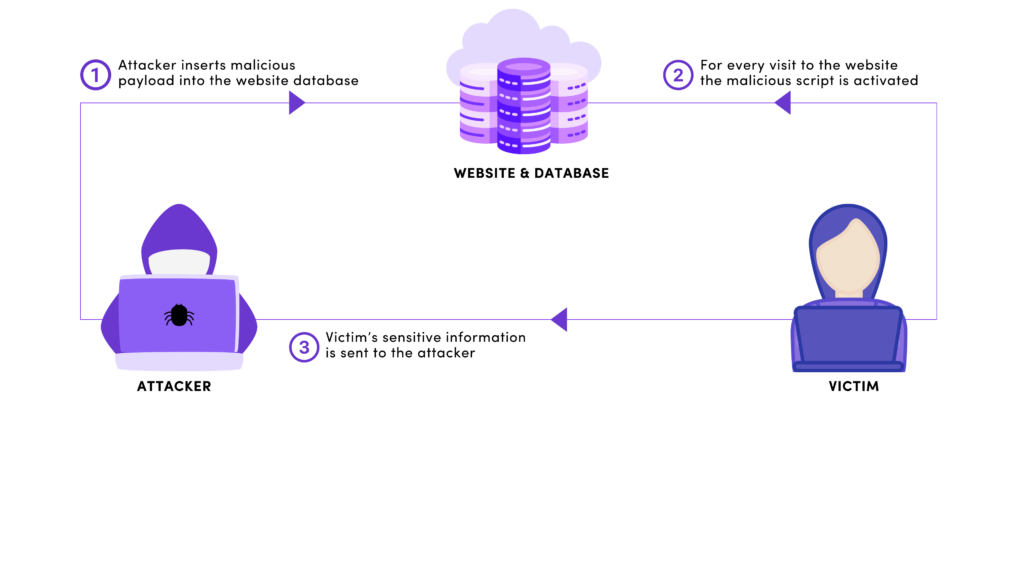
Cross-Site Scripting (XSS) is a vulnerability that allows attackers to inject malicious scripts, usually JavaScript, into web pages viewed by other users. This happens when a website fails to properly validate and sanitize user inputs. These malicious scripts execute in the user’s browser, enabling attackers to steal data or manipulate web content. XSS exploits the trust users have in a website, which makes it a dangerous and persistent threat.
XSS attacks are common on websites that accept user-generated content, like comment sections or form inputs. When user data is not properly sanitized, it creates an opening for attackers to insert harmful code.
Types of Attacks
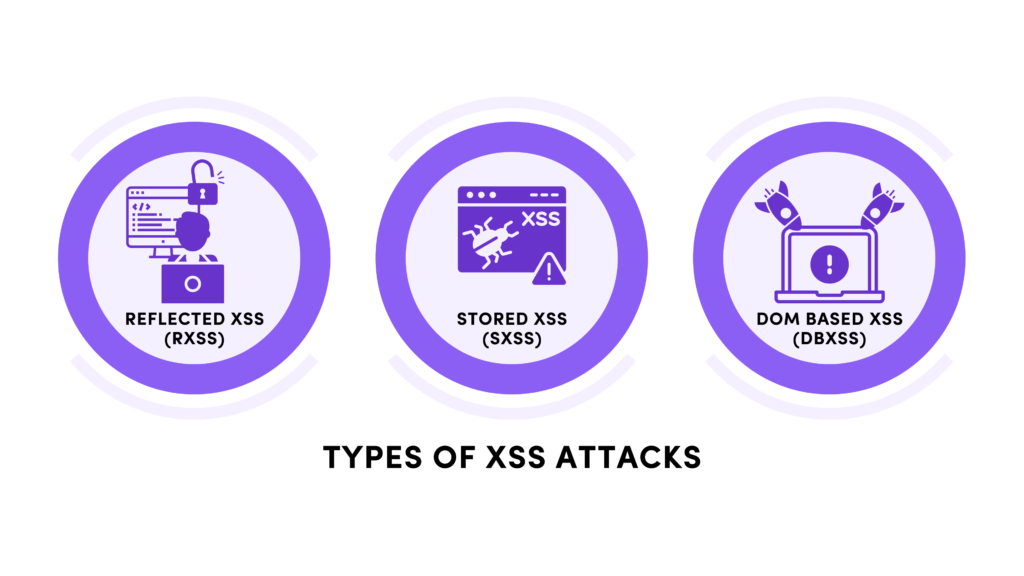
XSS attacks come in three main forms: Stored XSS, Reflected XSS, and DOM-based XSS. Each of these methods exploits different parts of a web application, but the ultimate goal remains the same: executing harmful scripts in the victim’s browser.
1. Stored XSS
Stored XSS is the most dangerous form because the malicious script is permanently saved on the server. When users load a page containing the script, it automatically executes in their browsers. For example, an attacker might inject malicious code into a website’s comment section. Each time someone views the comment, the harmful script runs in their browser, potentially stealing session cookies or login credentials.
2. Reflected XSS
In reflected Cross-Site Scripting attacks, the malicious script is embedded in a URL or a form parameter. The script is executed immediately when the user clicks on a specially crafted link. Unlike stored XSS, the script is not saved on the server but is reflected back to the user. This form of XSS is often used in phishing campaigns, where attackers trick users into clicking links that run harmful scripts.
3. DOM-based XSS
DOM-based XSS attacks exploit vulnerabilities in the Document Object Model (DOM), which is the structure that represents the content of a web page. Instead of injecting code into the website’s HTML, attackers manipulate the DOM to execute malicious scripts. This attack type relies on how the website processes user input and dynamically updates the page content.
Impact of XSS Attacks
Cross-Site Scripting attacks can have severe consequences for both users and website owners. Here are some of the key impacts:
1. Data Theft
Cross-Site Scripting attacks can be used to steal sensitive user data, including cookies, session tokens, login credentials, and credit card information. Since the malicious script runs in the user’s browser, attackers can easily capture this data and send it to an external server they control.
2. Session Hijacking
One of the most dangerous outcomes of XSS is session hijacking. By stealing session cookies, attackers can impersonate the victim and gain unauthorized access to their accounts. This can lead to serious breaches, such as unauthorized transactions or data exposure.
3. Website Defacement
Malicious scripts can alter the content of a website, defacing it with unwanted or offensive material. This type of attack can damage the reputation of a website or business, leading to loss of trust from users.
4. Malware Distribution
XSS can also be used to distribute malware to users. For example, an attacker might inject a script that silently downloads malicious software onto the user’s computer, leading to a broader security compromise.
5. Phishing Attacks
XSS can be leveraged to create convincing phishing attempts. By altering the content on a website, attackers can insert fake login forms or messages that trick users into providing their personal information.
Cross-Site Request Forgery (CSRF) and Its Relationship with XSS
Cross-Site Request Forgery (CSRF) is another serious security vulnerability that can be used alongside XSS. While XSS involves executing malicious scripts in a user’s browser, CSRF tricks the user’s browser into making unauthorized requests to a website. For example, an attacker might craft a link that performs an action, like changing account settings, on a website without the user’s consent.
While XSS and CSRF are separate vulnerabilities, they can complement each other. For example, an attacker could use XSS to steal session cookies and then leverage CSRF to perform unauthorized actions on behalf of the user. To protect against both, developers must implement strong security measures and validation.
Prevention Strategies Against XSS
Preventing Cross-Site Scripting attacks requires a multi-layered approach. Here are several effective strategies:
1. Input Validation
One of the most important steps in preventing XSS is validating user input. Any data entered by users, whether through forms or URL parameters, should be sanitized to remove potentially harmful characters like <script> tags. This ensures that malicious code cannot be injected into the website.
2. Output Encoding
Output encoding ensures that any special characters in user input, such as <, >, and “, are converted into HTML-safe entities before being rendered on the page. This prevents the browser from interpreting them as executable code.
3. Content Security Policy (CSP)
Implementing a Content Security Policy (CSP) adds an extra layer of defense by restricting where scripts can be loaded from. A well-defined CSP can prevent malicious scripts from executing, even if they are injected into the page.
4. Regular Security Audits
Regular security audits are essential for identifying and fixing potential vulnerabilities in your website. Automated tools can scan for XSS weaknesses, but manual testing and code reviews are also crucial for uncovering more complex issues.
5. Secure Coding Practices
Adopting secure coding practices is key to preventing XSS attacks. This includes using frameworks that automatically handle input validation and output encoding, as well as following best practices for user input handling. Secure coding can significantly reduce the likelihood of introducing vulnerabilities.
If you are looking for the answer to the question: How to prevent cross site scripting, this point of the blog can help you!
Protect Your Website from XSS Attacks with Axipro’s Expert Security Services
Ensure your website’s security with Axipro’s Vulnerability Assessment and Penetration Testing services. Our expert team will identify and fix potential XSS vulnerabilities before attackers can exploit them. With our comprehensive testing and proactive security measures, you can safeguard sensitive user data and prevent damaging breaches. Don’t wait until it’s too late—protect your site today with Axipro’s trusted security solutions and stay one step ahead of cyber threats!
Conclusion
Cross-Site Scripting attacks remain a significant threat to web security. Whether it’s through stored, reflected, or DOM-based XSS, attackers can use these vulnerabilities to steal data, hijack sessions, or deface websites. Protecting your site from XSS requires input validation, output encoding, and security policies like Content Security Policy (CSP). Understanding how XSS and Cross-Site Request Forgery (CSRF) attacks work together can also help in developing a more comprehensive security strategy. By implementing best practices and staying vigilant, web developers can minimize the risks posed by these attacks and provide a safer online experience for users.
