Overview – This blog offers a concise yet compelling conclusion to your ISO 27001 journey, highlighting why certification is a strategic move for businesses of all sizes. It recaps the value of implementing an ISO 27001 management system, emphasizes the importance of proactive data security, and encourages organizations to take the next step toward compliance. You’ll also find clear answers to common questions about ISO 27001 certification, audits, and consultants. Whether you’re just starting with a gap analysis or preparing for your certification audit, this guide—powered by Axipro—will help you move forward with confidence and clarity.
TL;DR
- ISO 27001 certification is a powerful way to strengthen your business’s data security, build trust, and meet global compliance standards.
- This blog highlights the benefits of implementing an ISO 27001 management system, explains key certification steps, and answers FAQs about audits, consultants, and requirements.
- Whether you’re a small business or an enterprise, Axipro can help you prepare with a gap analysis, streamline the certification process, and ensure long-term compliance.
What Is ISO 27001 and Why Does It Matter?
ISO 27001 is an international standard developed by ISO and IEC, focused on how organisations manage information security. As part of the broader ISO 27000 family, this standard outlines the structure for implementing an effective ISO 27001 management system. It’s not just a document—it’s a strategic approach to safeguarding your digital and physical assets.
Why Get ISO 27001 Certified?
Investing in ISO 27001 certification pays off in multiple ways. Here’s what your business gains:
- Stronger Data Security: From employee records to customer databases, your data is protected from unauthorized access and cyberattacks.
- Compliance Assurance: Meet critical ISO 27001 certification requirements and stay aligned with regulations like GDPR, HIPAA, and more.
- Market Advantage: Certification sets you apart from competitors and can even become a deal-clincher for new contracts.
- Customer Confidence: Clients are more likely to trust a business with verifiable security practices.
Operational Clarity: Standardized controls lead to smoother internal processes and clear accountability.
Core Principles Behind ISO 27001
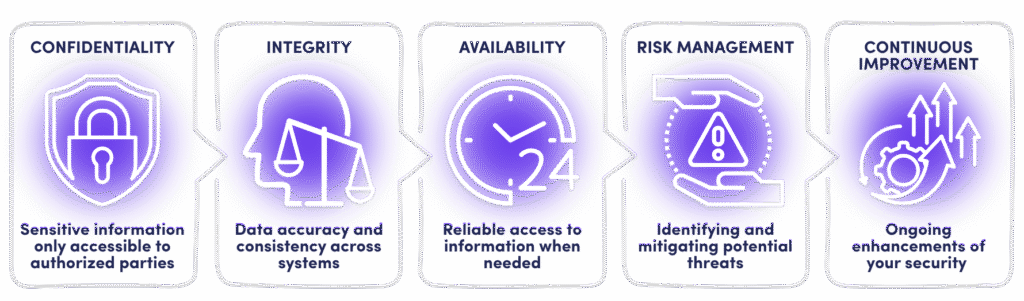
At its heart, ISO 27001 is built on five essential pillars:
- Confidentiality – Ensuring sensitive information is only accessible to authorized parties
- Integrity – Maintaining data accuracy and consistency across systems
- Availability – Guaranteeing reliable access to information when needed
- Risk Management – Proactively identifying and mitigating potential threats
- Continuous Improvement – Ongoing enhancements to your security framework
These principles form the foundation of a well-functioning ISO 27001 management system.
Key Components of ISO 27001 Certification
1. Information Security Management System (ISMS)
The ISMS is the heart of ISO 27001. It defines how your organization manages information security through a structured set of policies, procedures, and controls. The ISO 27001 management system ensures consistent security practices across departments, reducing vulnerabilities and improving trust.
2. Risk Assessment and Treatment
Effective security starts with knowing your weak points. Risk assessments identify potential threats and vulnerabilities, while treatment plans help you mitigate those risks. This strategic approach keeps your business protected, adaptive, and resilient.
3. Statement of Applicability (SoA)
The SoA outlines which controls from Annex A your organization applies and why. It’s a cornerstone document during any ISO 27001 certification audit—showing that you’ve made thoughtful, justified choices in your security framework.
4. Control Objectives and Controls (Annex A – 93 Controls)
Annex A consists of 93 controls categorized into themes like access control, cryptography, and incident management. Selecting and implementing the right controls is crucial for passing your ISO 27001 audit and maintaining long-term compliance.
5. Continuous Improvement (PDCA Cycle)
The ISO 27001 Certification Process
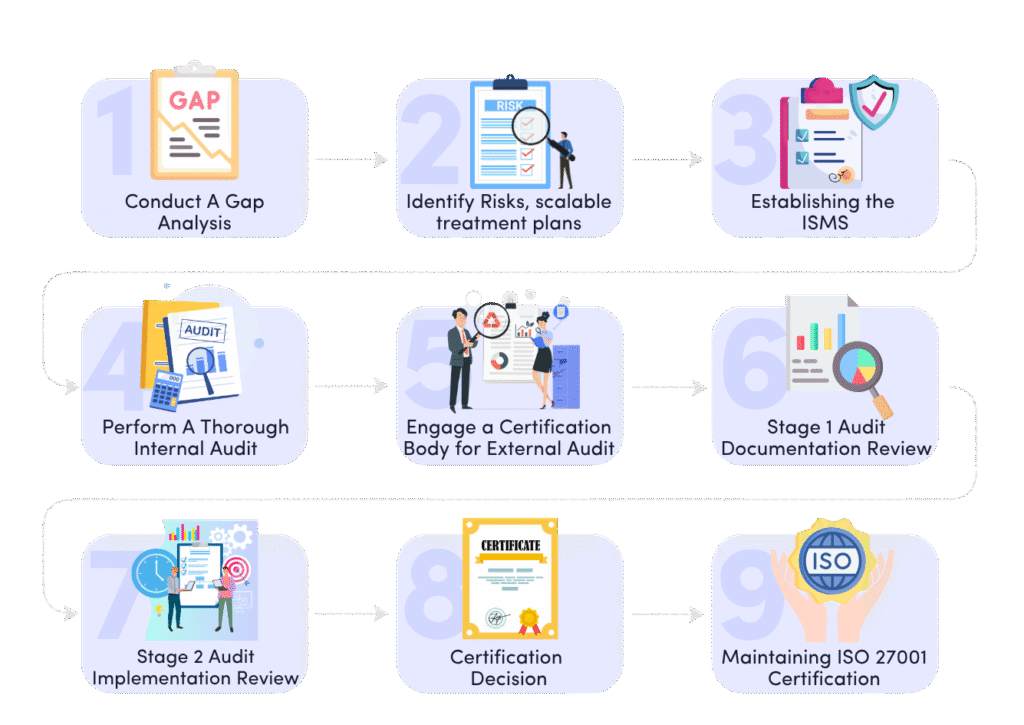
Achieving ISO 27001 certification requires careful planning, gap analysis, assessment, and implementation, and it is not an overnight process. The goal is to build a robust Information Security Management System (ISMS) that aligns with the ISO 27001 standard and demonstrates your organization’s commitment to managing information security risks effectively.
Here’s a detailed breakdown of the certification process:
1. Define the Scope of Your ISMS
The first step is to define the scope of your ISO 27001 information security management system certification. This involves identifying which parts of your organization and its information systems will be covered under the certification. Depending on your business’s size and structure, the scope might include the entire organization, specific business units, or particular IT systems.
2. Perform a Risk Assessment
Once the scope is defined, the next step is conducting a risk assessment. This is critical in the ISO 27001 certification process as it helps you identify potential security risks to your information assets. Risks can stem from various sources, including cyber threats, human error, or physical hazards.
- Steps in Risk Assessment:
- Identify Risks: Identify potential risks that could affect the confidentiality, integrity, or availability of your information.
- Analyze Risks: Assess the likelihood and potential impact of each risk.
- Prioritize Risks: Rank risks by severity so you can address the most critical ones first.
3. Implement Security Controls
Following the risk assessment, you’ll need to implement appropriate security controls to mitigate or eliminate those risks. ISO 27001 provides a comprehensive set of 93 controls in Annex A, categorized into 4 areas such as access control, incident management, and physical security.
4. Develop Documentation and Policies
Documentation is a key part of the ISO 27001 certification process. Proper documentation demonstrates that your ISMS is functioning as intended.
Essential documents include:
- ISMS Policy: Outlines your organization’s information security objectives and the framework to achieve them.
- Risk Assessment Report: Records the risks identified during the assessment.
- Statement of Applicability (SoA): Lists the security controls your organization has implemented, including justifications for any exclusions.
- Risk Treatment Plan: Details how your organization will mitigate or address the identified risks.
These documents serve as key evidence during the certification audit.
5. Conduct Internal Audit
Before the external audit, an internal audit must be conducted to ensure the ISMS is functioning effectively and meeting ISO 27001 requirements. This internal review helps to uncover any weaknesses or nonconformities, allowing you to address them before the official audit.
6. Engage a Certification Body for External Audit
Once your internal audit is complete, it’s time to engage an accredited certification body to conduct the external audit. This audit takes place in two stages:
- Stage 1: Documentation Review: The auditor reviews your ISMS documentation to ensure it aligns with ISO 27001 requirements.
- Stage 2: Certification Audit: The auditor evaluates the implementation of your ISMS by interviewing staff, inspecting facilities, and reviewing processes for compliance with your ISMS policies.
If your ISMS meets the ISO 27001 certification requirements, your organization will be awarded certification.
7. Maintaining ISO 27001 Certification
Achieving certification is just the beginning. To maintain certification, your organization must continually update and improve the ISMS. ISO 27001 requires annual surveillance audits and a full recertification audit every three years.
- Surveillance Audits: Conducted annually by the certification body to ensure your ISMS remains compliant with the ISO 27001 standard.
- Recertification Audit: A more comprehensive audit that occurs every three years to maintain your ISO 27001 certification status.
At Axipro, we help businesses navigate the certification journey, reduce risks, and strengthen trust with clients.
ISO 27001 Certification Requirements: Clause Breakdown
- Clause 4: Understand your organization’s context and interested parties.
- Clause 5: Leadership involvement is non-negotiable—top-level accountability matters.
- Clause 6: Planning must include risk-based thinking and measurable objectives.
- Clause 7: Support via resources, competence, and communication.
- Clause 8: Day-to-day operations must align with your ISMS scope.
- Clause 9: Measure performance through monitoring and internal audits.
- Clause 10: Act on audit findings and improve continuously.
Annex A: Implement relevant controls that align with business risks.
Common Challenges During ISO 27001 Certification Implementation
1. Resistance to Change
2. Lack of Top Management Commitment
A successful ISO 27001 management system needs executive-level backing. Without visible leadership support, teams may lack motivation, and key resources can be delayed. Aligning your security goals with business objectives is key to getting C-suite buy-in.
3. Inadequate Risk Assessment
4. Documentation Overload
5. Time and Resource Constraints
Mesh ID Achieves ISO 27001 with Axipro in Just 6 Weeks
They provide the best value for money for our ISO 27001 audit readiness. Seriously, if you don't go with Axipro...you made a bad decision.
How to Prepare for ISO 27001 Certification
1. Appoint an Internal Team or Hire an ISO 27001 Consultant
Depending on your internal expertise, forming a capable team or bringing in an ISO 27001 consultant is a smart first step. Consultants bring experience that can cut through uncertainty and fast-track your certification efforts.
2. Define Clear Roles and Responsibilities
3. Create a Roadmap with Realistic Timelines
4. Conduct Staff Training and Awareness Programs
5. Use ISO 27001 Implementation Tools and Templates
Get a comprehensive ISO guideline
Maintaining Compliance After Certification
1. Surveillance Audits
2. Conduct Regular Risk Assessments
3. Update Controls as Needed
4. Keep Documentation Current
5. Promote Ongoing Employee Engagement
ISO 27001 vs Other Information Security Standards
ISO 27001 vs ISO 27002:
ISO 27001 vs SOC 2:
ISO 27001 vs NIST:
Which is right for your business?
ISO 27001 Certification Cost and Duration
- Company size and complexity of operations
- Existing documentation and systems
- Whether you’re doing internal work or hiring an ISO 27001 consultant
How to Choose the Right Certification Body
- Accreditation and credibility: Work with an accredited body that’s globally recognized.
- Industry experience: Ensure they understand your sector’s risks and language.
- Cost transparency: Clear breakdowns with no hidden fees.
- Ongoing support: Will they assist post-certification or during your next ISO 27001 certification audit?
At Axipro, we’ve guided businesses through every step of their journey. Whether you’re in healthcare, finance, SaaS, or manufacturing, our team ensures your ISO 27001 efforts are smooth, strategic, and worth every dollar.
Final Thoughts on ISO 27001 Certification: Why Now Is the Time to Act
As cyber threats continue to evolve and data becomes a core business asset, protecting your information systems is no longer optional — it’s essential. ISO 27001 certification isn’t just another compliance checkbox. It’s a strategic business decision that builds credibility, ensures regulatory alignment, and demonstrates your commitment to safeguarding customer and company data.
For businesses looking to establish long-term trust, streamline risk management, and stand out in competitive markets, implementing an ISO 27001 management system is a smart move. It signals to stakeholders that you’re serious about information security and proactive in tackling risks before they become costly incidents.
Whether you’re a startup handling customer data or an established enterprise aiming to meet international security standards, investing in ISO 27001 certification requirements is a forward-thinking step. It future-proofs your operations, keeps you ahead of potential breaches, and creates a culture of accountability and awareness throughout your organisation.
Frequently Asked Questions (FAQ)
Is ISO 27001 mandatory?
How long does certification last?
Once achieved, ISO 27001 certification is valid for three years. However, you’ll need to undergo ISO 27001 audit surveillance annually to maintain your status and prove ongoing compliance.
Can small businesses get ISO 27001 certified?
Absolutely. In fact, small businesses often benefit the most. It shows maturity and readiness, especially when competing for contracts. A tailored ISO 27001 management system can be scaled according to your size and risk profile.
Do I need a consultant?
While not required, working with an experienced ISO 27001 consultant can significantly speed up the process, reduce costly mistakes, and prepare you more effectively for the ISO 27001 certification audit. At Axipro, we help businesses avoid the guesswork and get certification-ready with clarity and confidence.