Share This Post
Data security is paramount in today’s digital landscape. As organizations handle increasingly sensitive customer data, achieving SOC 2 compliance has become essential for building trust and maintaining compliance. But what exactly is SOC 2 compliance, and how can your organization achieve it? This comprehensive guide provides step-by-step instructions for beginners, ensuring you have the knowledge and resources to succeed.
Outline
What is SOC 2 compliance?
Why is SOC 2 Compliance Important?
- Customer Trust
- Competitive Advantage
- Risk Mitigation
- Regulatory Alignment
When to Choose SOC 2 Instead of SOC 1 and SOC 3
Step 1: Understand SOC 2 Requirements
Step 2: Define Your Scope
Step 3: Conduct a Gap Analysis
Step 4: Implement Required Controls
Step 5: Choose a SOC 2 Auditor
Step 6: Conduct a Readiness Assessment
Step 7: Undergo the SOC 2 Audit
Step 8: Maintain SOC 2 Compliance
Who Needs SOC 2 Compliance?
FAQs
What is SOC 2 Compliance?
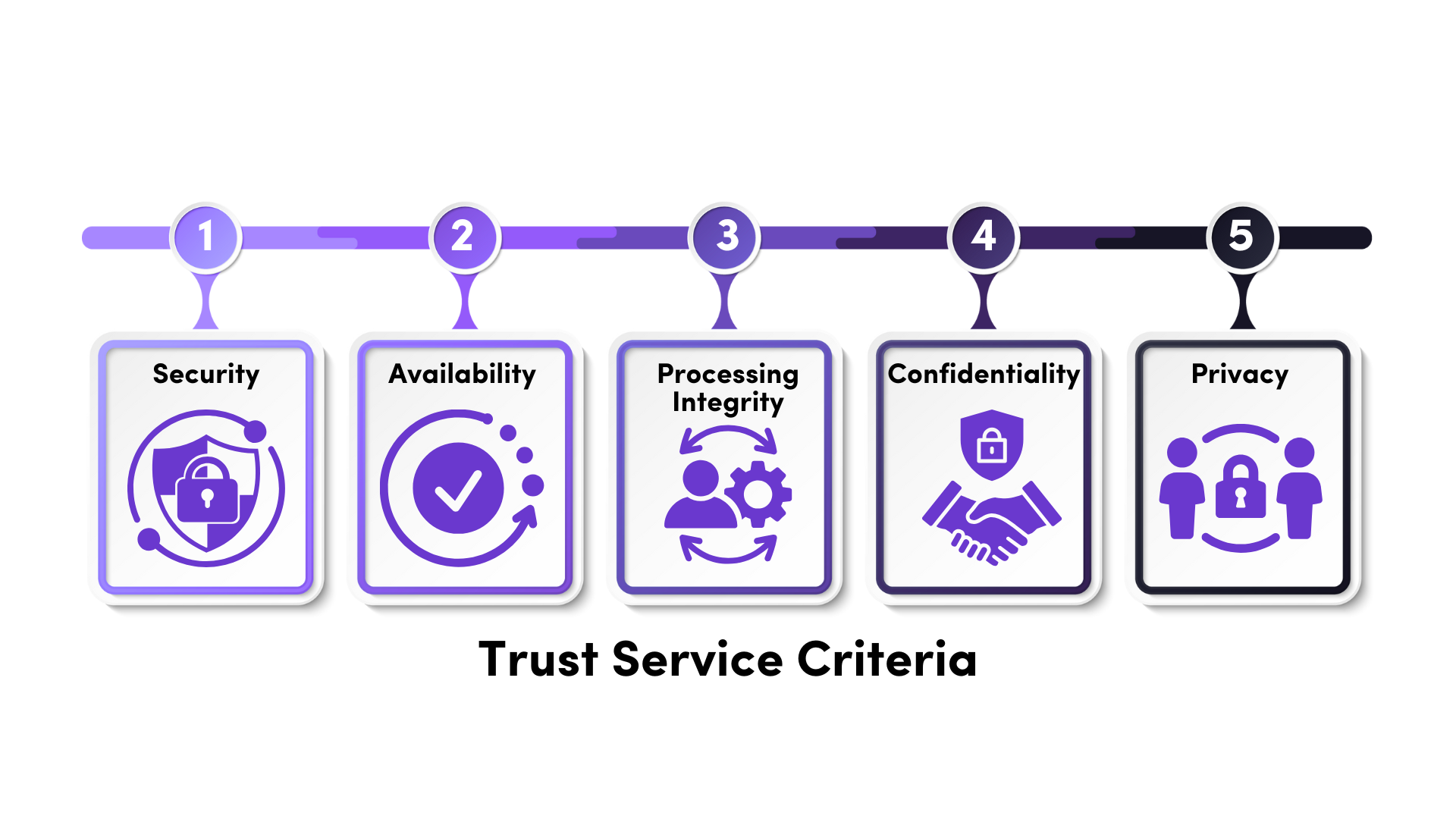
SOC 2 (Service Organization Control 2) certification is a globally recognized standard for managing customer data based on five Trust Service Criteria (TSC): Security, Availability, Processing Integrity, Confidentiality, and Privacy. Developed by the American Institute of Certified Public Accountants (AICPA), SOC 2 reports demonstrate that your organization adheres to best practices for safeguarding data.
Unlike other compliance standards, SOC 2 is tailored to each organization’s unique needs. It’s not a one-size-fits-all framework; instead, it emphasizes a company’s specific commitments to data security.
Why is SOC 2 Compliance Important?
Achieving SOC 2 certification is more than just a checkbox for businesses handling sensitive customer data; it is a strategic move that builds trust, reduces risk, and aligns your organization with regulatory and industry expectations. The significance of SOC 2 compliance cannot be overstated, especially in today’s world, where data breaches and security concerns are rampant. Here’s why it’s important and the benefits it brings:
Customer Trust
In an age where consumers are increasingly aware of data security issues, demonstrating SOC 2 compliance is a powerful way to reassure your customers. A SOC Type 2 report signals to clients and stakeholders that your organization is committed to protecting their sensitive information and has the necessary controls. This assurance fosters loyalty and long-term relationships, giving your organization a competitive edge in the marketplace.
Competitive Advantage
SOC 2 compliance meets customer expectations and sets you apart from competitors. Many organizations include SOC 2 certification as a criterion for selecting vendors or partners. A SOC Type 2 report demonstrates your commitment to adhering to high standards and provides tangible proof of your dedication to data security. This differentiation can open doors to new business opportunities, especially in industries such as technology, healthcare, and finance.
Risk Mitigation
Data breaches can lead to financial losses, reputational damage, and even legal consequences. By following SOC 2 standards, your organization proactively minimizes vulnerabilities, implements robust controls, and ensures that sensitive data is safeguarded. This reduces the likelihood of security incidents and mitigates the impact of potential breaches, enabling you to act swiftly and effectively when challenges arise.
Regulatory Alignment
Compliance with SOC 2 requirements aligns your organization with broader regulatory frameworks, simplifying legal and audit processes. Whether you’re dealing with HIPAA, GDPR, or other regulations, the practices and controls established through SOC 2 often overlap with these requirements, ensuring a streamlined approach to compliance. This alignment can also ease cross-border data management challenges for organizations handling international customers.
Whether you’re a SaaS provider, a cloud-based service, or any business that processes customer data, achieving SOC 2 compliance is a critical milestone in establishing your organization as a trustworthy and reliable partner
When to Choose SOC 2 Instead of SOC 1 and SOC 3
If your organization handles sensitive customer data but is not directly involved in financial reporting, SOC 2 is the right choice. Unlike SOC 1, which focuses solely on financial controls, SOC 2 evaluates your overall data security, privacy, and compliance practices—making it essential for SaaS providers, cloud service companies, and security-focused businesses. While SOC 3 is a public-facing summary, it lacks the detailed insights that clients and partners often require for due diligence. If you need to demonstrate strong security controls to customers, auditors, or regulators, SOC 2 provides the necessary depth and assurance.
Step 1: Understand SOC 2 Requirements
To embark on the SOC 2 certification journey, it’s essential to understand the framework’s key components. SOC 2 revolves around five Trust Service Criteria, the foundation of the certification process. Each criterion outlines specific areas of focus for managing and securing customer data effectively:
- Security: This criterion is mandatory for all SOC 2 audits and addresses measures to protect systems and data against unauthorized access, breaches, and other security threats. It includes controls such as firewalls, multi-factor authentication, and intrusion detection systems.
- Availability: This criterion ensures that your systems and services are operational and meet customer expectations. It involves system monitoring, disaster recovery planning, and uptime maintenance.
- Processing Integrity: Ensuring that data processing is complete, valid, accurate, and authorized is critical. This criterion covers controls to validate data inputs, process flows, and outputs.
- Confidentiality: Protecting sensitive information from unauthorized disclosure is a priority. This involves encryption, access controls, and secure data storage practices.
- Privacy: Handling personal information in compliance with privacy regulations and customer expectations is vital. This criterion ensures that data collection, storage, and sharing practices align with privacy laws such as GDPR.
Understanding these criteria helps you tailor your approach to align with your organization’s unique operations, ensuring a smoother path to compliance.
Step 2: Define Your Scope
Defining the scope of your SOC 2 audit is a foundational step that determines the audit’s focus and complexity. Proper scoping ensures that your resources are utilized efficiently and that the audit delivers meaningful insights. Here’s how to define your scope effectively:
- Identify Key Systems: Focus on systems, applications, and services that handle or interact with customer data. This includes databases, cloud platforms, and software applications.
- Choose Relevant Criteria: While the Security criterion is mandatory, decide which additional Trust Service Criteria (Availability, Processing Integrity, Confidentiality, Privacy) are applicable based on your business model and customer requirements.
- Assess Business Processes: Map out workflows, data handling practices, and system interactions to ensure alignment with SOC 2 standards.
A well-defined scope prevents unnecessary audits and ensures that your efforts are focused on the areas that matter most to your stakeholders.
Step 3: Conduct a Gap Analysis
A gap analysis is a critical step that identifies where your organization’s current practices fall short of SOC 2 requirements. This process lays the groundwork for implementing necessary changes and preparing for the audit. Here’s how to conduct a thorough gap analysis:
- Evaluate Existing Controls: Review your security policies, procedures, and technical safeguards. This includes examining access controls, incident response protocols, and data encryption measures.
- Highlight Weaknesses: Identify gaps or vulnerabilities in your systems, such as outdated software, insufficient monitoring, or untrained personnel.
- Prioritize Improvements: Create a roadmap to address deficiencies, starting with high-risk areas. Assign clear responsibilities and timelines to ensure progress.
By conducting a gap analysis, you clearly understand your organization’s readiness and can focus your efforts on the areas that need the most attention.
Step 4: Implement Required Controls
Once you’ve identified gaps, the next step is implementing controls aligning with your audit scope and the Trust Service Criteria. These controls serve as the foundation for demonstrating compliance and ensuring data security. Key actions include:
- Developing Security Policies: Establish comprehensive policies that address key areas such as access controls, incident response, data encryption, and employee training.
- Training Employees: Educate your team on SOC 2 requirements and their roles in maintaining compliance. Regular training sessions help build a security-first culture.
- Monitoring Systems: Deploy tools for real-time monitoring of networks, applications, and endpoints to detect and respond to potential threats promptly.
- Documenting Processes: Maintain detailed records of all procedures, controls, and activities. This documentation serves as evidence during the audit and ensures consistency.
Effective implementation of these controls ensures your organization’s readiness for the audit process and sets the stage for long-term compliance.
Step 5: Choose a SOC 2 Auditor
Selecting the right auditor is a crucial decision that impacts the success of your SOC 2 certification journey. A qualified and experienced auditor evaluates your compliance and provides valuable guidance. Here’s what to consider:
- Qualifications: Ensure that the auditor is a licensed CPA or affiliated with a reputable firm specializing in SOC 2 audits.
- Industry Experience: Choose an auditor familiar with your industry and its unique challenges. This ensures that their insights are relevant and actionable.
- Reputation: Research the auditor’s track record, client testimonials, and case studies to gauge their expertise and reliability.
A knowledgeable auditor helps navigate the complexities of the audit process and ensures that your organization is well-prepared.
Step 6: Conduct a Readiness Assessment
Before undergoing the official SOC 2 audit, conducting a readiness assessment is advisable. This preliminary evaluation helps:
- Evaluate Preparedness: Confirm that all required controls are in place and functioning effectively.
- Test Processes: Simulate audit scenarios to identify potential issues or gaps in implementation.
- Fine-Tune Controls: Address any remaining weaknesses and optimize performance to ensure compliance.
A readiness assessment minimizes surprises during the official audit and boosts your confidence in achieving certification.
Step 7: Undergo the SOC 2 Audit
The SOC 2 audit involves a thorough evaluation of your organization’s controls. Depending on your goals, you may undergo one of two types of audits:
- Type 1 Audit: This evaluates your controls at a specific point in time, focusing on their design and implementation.
- Type 2 Audit: This assesses the effectiveness of your controls over a defined period (typically 3-12 months), providing a more comprehensive view of your compliance efforts.
During the audit, the auditor will:
- Review your documentation.
- Test the implementation and effectiveness of controls.
- Provide feedback on areas for improvement.
Upon completion, you’ll receive a SOC 2 report detailing your compliance status and any recommendations.
Step 8: Maintain SOC 2 Compliance
Achieving SOC 2 certification is not a one-time effort. To sustain compliance and protect customer trust, ongoing efforts are required:
- Regular Monitoring: Continuously monitor systems and processes for vulnerabilities and ensure controls remain effective.
- Annual Audits: Schedule periodic audits to renew your certification and address evolving risks.
- Policy Updates: Revise your policies and controls to adapt to regulations, technology, and business operations changes.
Employee Training: Keep your team informed about evolving compliance requirements and security best practices.
Who Needs SOC 2 Compliance?
Although SOC 2 compliance is not legally required, it is a crucial standard for businesses handling sensitive client data, demonstrating their commitment to security, availability, and privacy. It is particularly valuable for B2B service providers operating in industries where data protection is a top priority.
Key industries that benefit from SOC 2 compliance include:
Healthcare providers, such as hospitals and telemedicine platforms, where protecting patient data is essential.
Financial institutions, including banks and payment processors, which handle highly sensitive personal and financial data.
Managed service providers, like IT and security firms, that access and manage client systems.
Cloud service providers and data centers, which store critical business and personal data for various clients.
B2B and B2B2C SaaS companies, where safeguarding proprietary business data is key.
Education providers, such as online learning platforms, that manage student and institutional data.
Beyond industry-specific needs, businesses often pursue SOC 2 compliance at key growth stages. Scaling operations requires formalizing security processes, while entering regulated markets demands adherence to strict security measures. Additionally, meeting customer demands becomes a driving factor as businesses expand—clients increasingly expect strong security assurances.
For companies handling sensitive data, SOC 2 compliance is a strategic investment that strengthens security, builds trust, and supports long-term business success.
FAQs
- What is the difference between SOC Type 1 and SOC Type 2?
SOC Type 1 focuses on controls at a specific point in time, while SOC Type 2 evaluates their effectiveness over a period (e.g., 6-12 months).
- How long does it take to achieve SOC 2 certification?
The timeline varies depending on your organization’s readiness, but it typically takes 6-12 months to implement controls and complete the audit.
- Is SOC 2 mandatory?
SOC 2 is not legally mandatory but is often required by clients and partners to ensure data security.
- How much does SOC 2 certification cost?
Costs vary widely based on factors like audit scope, organization size, and auditor fees. Expect to invest between $20,000 and $100,000.
- Can small businesses achieve SOC 2 compliance?
SOC 2 is achievable for businesses of all sizes with proper planning and resources.
Achieving SOC 2 certification may seem challenging, but with the right approach, it’s attainable. By following this guide from Axipro, your organization can strengthen its data security practices, build customer trust, and gain a competitive edge in the marketplace.